udp flood v1.0 Free Download
udp flood v1.0 Free Download
A UDP flood is a type of Denial of Service (DoS) attack in which a large number of User Datagram Protocol (UDP) packets are sent to a targeted system in an attempt to overload it and prevent it from functioning properly. The attacker does not need to spoof the UDP packets’ source IP address, as UDP is a connectionless protocol. This makes UDP floods more difficult to detect and stop than other types of DoS attacks.

UDP flooding is a type of Denial of Service (DoS) attack in which a malicious user sends large amounts of UDP traffic to a targeted server in order to overwhelm it and prevent legitimate users from being able to access the server. This can be done by sending a large number of UDP packets with incorrect checksums, or by sending UDP packets with forged source IP addresses.
A UDP flood is a type of Denial of Service (DoS) attack in which a hacker sends a high volume of UDP packets to a targeted system in order to overwhelm it and cause it to crash or become unresponsive. This type of attack can be difficult to detect and can be very disruptive, making it a popular choice among hackers.
Software With Crack
A UDP flood is a DoS attack using the User Datagram Protocol. The attacker sends large numbers of UDP packets to random ports on a remote host with the intention of overwhelming that host’s ability to process them. This can cause the target host to crash, reboot, or become too slow to respond to legitimate traffic. A UDP flood is sometimes called a “bandwidth flood” because it uses up all of the bandwidth available on the target network.
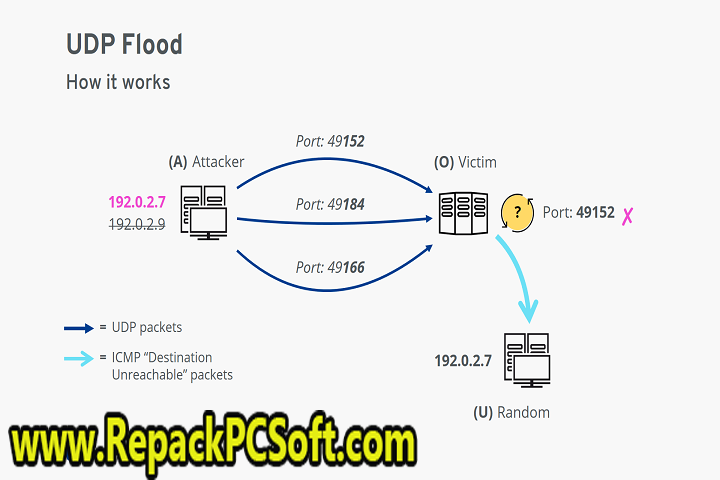
A UDP flood attack can be initiated in several ways. The most common is to use a botnet—a collection of malware-infected computers that are controlled by a attacker—to send large numbers of UDP packets to a single target. The attacker can also spoof the source IP address of the UDP packets so that it appears as if they are coming from multiple devices.
UDP flood attacks are one of the most common types of DDoS attacks. They work by flooding the target system with UDP packets. The target system then becomes overwhelmed and is unable to process legitimate requests. A UDP flood is a type of denial-of-service attack in which a large number of User Datagram Protocol (UDP) packets are sent to a targeted system in an attempt to overload it and prevent legitimate users from accessing services. UDP floods are often used in conjunction with other types of attacks, such as SYN floods, ICMP floods, and DNS amplification attacks.
Software With Patch
A UDP flood is a type of denial-of-service attack in which a large number of User Datagram Protocol (UDP) packets are sent to a targeted system in an attempt to overwhelm that system and prevent it from functioning properly. UDP floods are particularly effective because UDP is a connectionless protocol, which means that there is no need to establish a connection before sending data. As a result, it can be launched very quickly and can cause significant damage.
A UDP flood is a type of denial-of-service (DoS) attack in which a hacker sends a large number of User Datagram Protocol (UDP) packets to a target system in an attempt to overload it and prevent legitimate users from accessing the system. It are often used in distributed denial-of-service (DDoS) attacks, as they can be amplified by reflector servers. It are also sometimes called SYN floods, as they can exploit the same vulnerabilities as SYN floods.
A UDP flood is a type of Denial of Service (DoS) attack in which a large number of User Datagram Protocol (UDP) packets are sent to a targeted system in an attempt to overwhelm that system and cause it to crash. It are particularly effective because UDP is a “connectionless” protocol, which means that each UDP packet can be sent without first establishing a connection with the target system. This makes it very difficult for firewalls and other security systems to block UDP floods, since they often can’t tell the difference between legitimate traffic and malicious traffic.
You May Also Like :: OpenBullet
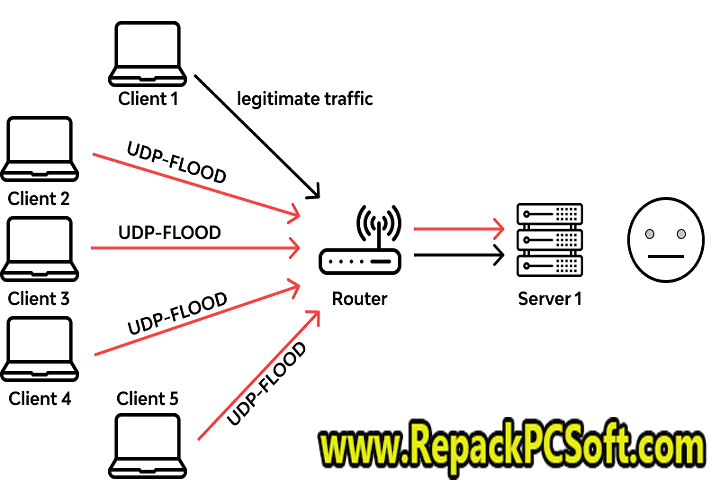
One way to protect against UDP floods is to use a network intrusion detection system (NIDS) that can detect and block suspicious traffic. Another way to defend against it is to rate-limit incoming UDP traffic so that only a certain number of packets can be processed per second. This will help prevent your system from being overwhelmed by too much traffic at once.
Download Link : Mega
Your File Password : RepackPCSoft.com
File Version & Size : 1.0 | 1.4 MB
File Type : Compressed / Zip & RAR (Use 7zip or WINRAR to unzip File)
Support US : All Windows (32-64Bit)
Upload By : Muhammad Usman
Virus Status : 100% Safe Scanned By Avast Antivirus




