SQL Injection Tool v2.1 Free Download
SQL Injection Tool v2.1 Free Download
SQL injection is a code injection technique that might destroy your database. SQL injection is one of the most common web hacking techniques. In SQL injection, malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection attacks are a type of injection attack, in which SQL code is injected into data-plane input in order to effect the execution of predefined SQL commands.

SQL injection must exploit a security vulnerability in an application’s software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database. SQL injection is a code injection technique that might destroy your database. SQL injection is one of the most common web hacking techniques. SQL injection attacks allow attackers to spoof identity, tamper with existing data, cause repudiation issues such as voiding transactions or changing balances, allow the complete disclosure of all data on the system, destroy the data or make it otherwise unavailable, and become administrators of the database server.
SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection must exploit a security vulnerability in an application’s software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed.
Software With Crack
SQL injection is a code injection technique that might destroy your database. It are one of the most common web hacking techniques. It allows attackers to insert malicious SQL code into an input field for execution (such as a username or email address). This code can then be used to access, modify, or delete data in your database. It attacks can be prevented by using parameterized queries or stored procedures. These methods ensure that the SQL code that is executed is not influenced by outside input.
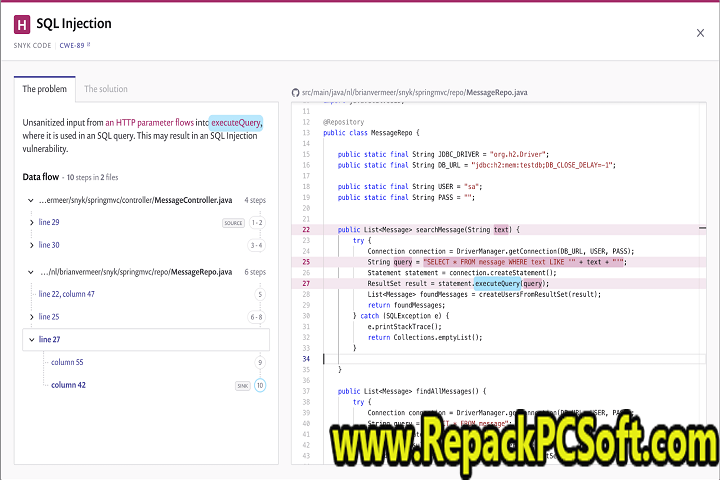
SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed. It allows an attacker to execute malicious SQL statements that control a web application’s database server, potentially allowing data manipulation and retrieval, as well as other malicious operations.
SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). It must exploit a security vulnerability in an application’s software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. It is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
Software With Patch
An SQL injection is when someone tries to insert malicious code into your website through a form field or URL parameter. If successful, the attacker can gain access to your database and run commands that could delete data, change table structure, or even expose sensitive information like credit card numbers or user passwords. If you manage a website, it’s important to keep up with security updates and patch any vulnerabilities as soon as possible. One type of vulnerability that you may need to deal with at some point is an SQL injection.
SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). Fortunately, there are steps you can take to prevent it from happening in the first place. One of the most important things you can do is to sanitize any user input before inserting it into your database. This means removing any characters that could be used to inject malicious code.
SQL injection is a code injection technique that might destroy your database. Patching your software is the only way to fix this dangerous vulnerability. You should also make sure that you’re using prepared statements when querying your database. Prepared statements help to protect against it attacks by separating the code that runs the query from the data that is inserted into the query. That way, even if someone tries to insert malicious code into a form field, it won’t be executed by the database.
You May Also Like To Download :: Proxy Fire Master
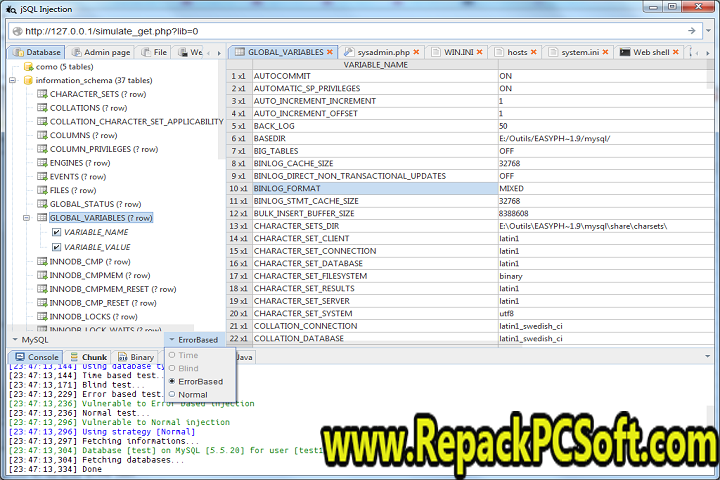
SQL injection must exploit a security vulnerability in an application’s software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. It is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
Download Link : Mega
Your File Password : RepackPCSoft.com
File Version & Size : 2.1 | 1002 KB
File Type : Compressed / Zip & RAR (Use 7zip or WINRAR to unzip File)
Support US : All Windows (32-64Bit)
Upload By : Muhammad Usman
Virus Status : 100% Safe Scanned By Avast Antivirus





